|
 
In the first installment of this 2019 Security Report we reviewed the latest trends and threats facing the dustry today.
In the second installment, we took a deeper look at the cyber crime underworld to get the democratization of cyber crime to understand how malware has shifted gears to a more stealth- like approach to infecting organizations. In this third installment we focus on how threat actors are able to keep one step ahead by targeting the weakest points in an organization’s IT infrastructure – the cloud, mobile and IoT. Indeed, these platforms offer a threat actor a much higher chance of success and fewer obstacles to overcome due to them being far less protected. As a result, their profits can often be higher due to more private data stored on mobile devices and larger databases and resources held in the cloud. So with account takeovers becoming increasingly common, and the introduction of GDPR in 2018, potential data breaches and other attacks are simply too costly to ignore.
在这份2019年安全报告的第一期中,我们回顾了当今IT安全行业面临的最新趋势和威胁。在第二部分中,我们深入了解了网络犯罪的涉黑组织,了解了网络犯罪的自主化,了解了恶意软件是如何转向一种更隐蔽的方式来感染组织的(来入侵渗透目标系统)。 Democratization 民主化 gears 齿轮
在这第三部分中,我们将重点介绍威胁行动者如何通过瞄准机构的IT基础设施中的薄弱环节——云、移动和物联网——来保持先人一步。实际上,这些平台为威胁行动者提供了更大的成功机会和更少的障碍,因为它们受到的保护要少得多。 Obstacles 障碍
因此,由于存储在移动设备上的私有数据更多,而存储在云中的数据库和资源更大,它们的利润往往更高。因此,随着账户接管变得越来越普遍,以及2018年GDPR的引入,潜在的数据泄露和其他攻击可能性太高,不容忽视。 Takeover 接管 breaches 资料外泄
Few are surprised by the popularity of thecloud. It offers flexible computing options at a fraction of the cost and time.Organizations can conveniently improve data storage and server processing oruse Software-as-a-Service (SaaS) products. 很少有人对云的流行感到惊讶。它提供了灵活的计算选项,只需花费很少的成本和时间。机构可以方便地改进数据存储和服务器处理,或者使用软件即服务(SaaS)产品。
Cloud computing has become an integralpiece of today’s IT infrastructure. Its ‘try before you buy’ and ‘pay as you go’models provide organizations with the ability to test the technology, andintegration with the cloud is fast and usually requires virtually noorganizational down time. 云计算已经成为当今IT基础设施的一部分。它的“购买前尝试”和“购买后付款”模式为机构提供了测试技术的能力,与云的集成速度很快,通常不需要机构停机。 However, much like other emergingtechnologies, the cloud can be abused. So it’s imperative to know itsvulnerabilities, especially the holes in security. 然而,就像其他新兴技术一样,云也可能被滥用。因此,有必要了解它的漏洞,尤其是安全漏洞。 91%
of organizations are concernedabout cloud security.
Source: 2018 Cloud Security Report, Dome9
C l o u d ’s W e a k e s t P o i n t s In brief, the main security challenges withthe cloud and the services it pro- vides include: 简而言之,云计算及其提供的服务面临的主要安全挑战包括: ExternalExposure –
Cloud services are typically accessedfrom any location and any device. All that’s needed is an internet connection.While ease of access can boost company agility, services running in the cloudversus those on premise are more likely to be breached. 外部公开——云服务通常可以从任何位置和被任何设备访问。所需要的只是一个互联网连接。尽管易访问性可以提高公司的灵活性,但在云中运行的服务相对于在云中运行的服务更容易被破坏。 OnlyDefault Security –
Typically, cloud services areprovided with only basic security which allows unrestricted open internet filesharing. This vulnerability can open the door to any number of malware attacks. 只有默认安全性——通常,云服务只提供基本安全性,允许不受限制地开放internet文件共享。这个漏洞可以为任何数量的恶意软件攻击打开大门。
Cloud services are vulnerable across threemain attack vectors:
云服务在三个主要攻击载体上都是脆弱的:
Account Hijacks –
Gaining unauthorized access to an individual or organization’semail or computer account for malicious purposes. In a Check Point survey,Account Hijacks were the biggest concern amongst customers and partners. 帐户劫持-获取未经授权的访问个人或组织的电子邮件或计算机帐户的恶意目的。在一个检查点的调查中,账户劫持是客户和合作伙伴最关心的问题 MalwareDelivery –
Propagation, especially through in-appfile sharing services, such as Box or One Drive cloud apps, in order to commita variety of cyber crimes. 恶意软件的传播,特别是通过应用程序内的文件共享服务,如Box或One Drive云应用,为了犯下各种网络犯罪 DataLeaks –
Whether intentionally or unintentionally,data leakage occurs with the seamlessness of sharing information with cloudservices. 数据泄漏——无论是有意还是无意,数据泄漏都是在与云服务无缝共享信息的情况下发生的。 Due to the cloud’s security challenges, theCheck Point Incident Response team is seeing an increase in security breacheswith cloud services, both with SaaS and Infrastructure-as-a-Service (IaaS)models. 由于云的安全挑战,check point附带的事件回应团队发现云服务(SaaS和基础设施即服务(IaaS))模型的安全漏洞越来越多。 18%
of organizations experienced acloud security incident in the past year.
Source: 2018 Cloud Security Report, Dome9
Despite the upward trend in securitybreaches with the cloud, however, 65% of IT professionals still underestimatethe damage they can cause. The obvious concern is that organizations are nottaking cloud security seriously enough. The breach of sensitive data held inthe cloud is a huge risk for an organization, and threat actors know it. Therate of cyber attacks against cloud-based targets is growing, and with littlesign it will slow down. 然而,尽管云安全漏洞呈上升趋势,65%的IT专业人士仍然低估了它们可能造成的损害。显而易见的问题是,机构没有足够重视云安全。对于一个机构来说,泄露存储在云中的敏感数据是一个巨大的风险,威胁行动者知道这一点。针对基于云的目标的网络攻击率正在增长,而且几乎没有迹象表明它会放缓。 When asked why they may not be securingtheir cloud assets, a full 30% of survey respondents believe security is theresponsibility of the cloud service provider. This negates recommendations thatcloud security follow the Mutual Responsibility model shared by the cloudprovider and the customer. 当被问及为什么他们不能保护他们的云资产时,整整30%的受访者认为安全是云服务提供商的责任。这否定了云安全遵循云提供商和客户共享的相互责任模型的规范。 65%
of IT professionals underestimatethe damage caused by attacks on the cloud. Source: Check Point Security ReportThreat Prevention Research among IT andSecurity Professionals, November 2018 CHECK POINT RESEARCH — 2019 SECURITY REPORT
|5 Whether an organization suffers afinancial, informational or reputational loss, the overall effect of a cloudattack can be devastating to a business. To understand the potential damage ofa cloud attack, let’s take a closer look at Account Hijacks. 无论一个机构是否遭受财务、信息或声誉损失,云攻击的总体影响都可能对企业造成毁灭性的影响。为了了解云攻击的潜在危害,让我们仔细看看帐户劫持。 1in 3
ITProfessionals still consider security tobe the responsibility of the cloudservice provider. Source: Check Point Security ReportThreat Prevention Research among IT andSecurity Professionals, November 2018 49%
of organizations are increasingtheir cloud security budget in the next year. Source: 2018 Cloud Security Report,Dome9
H o w D o A cc o u n t H i j a c k s O c c u r ?
To take over an account, the attacker mustfirst gain the victim’s trust. The most common method to achieve trust is touse social engineering. Phishing attacks are the most common method forstealing log-in credentials from unsuspecting users. 要接管一个帐户,攻击者必须首先获得受害者的信任。获得信任最常见的方法是使用社会工程。钓鱼攻击是从毫无戒心的用户那里窃取登录凭据的最常见方法。 Here’s how it typically works. The cybercriminal sends an “urgent” email from Microsoft support or another serviceprovider requesting a response from the victim. A click on a link in the emailwill allow the attackers to hijack the victim’s account. We’ve all seen these phony emails, yet peoplestill fall prey to the scheme. 这是它的典型工作方式。网络罪犯发送了一封“紧急”电子邮件-由微软支持或其他服务提供商索取受害者的响应。点击邮件中的链接,攻击者就可以劫持受害者的账户。我们都见过,了解这种伪造的电子邮件,但人们仍然会成为这个骗局的受害者。
After proceeding to click on the link andenter their log-in credentials when prompted, the unsuspecting victim may alsoreceive a push notification by SMS to his mobile device. This is mainly used toadd an extra element of authenticity to the phishing scam, which the victim,having already trusted the initial source of the attack, will also likelyapprove and continue as instructed. Of course, as the victim unknowinglyprovides these sensitive log-in details to the attacker, the attacker uses themto gain access to the victim’s SaaS account, for example, helping themselves tothe private and confidential information stored there. 在点击链接并在提示时输入登录凭证后,毫无防备的受害者也可能会收到发送到其移动设备的短信推送通知。这主要是为了给网络钓鱼骗局增加一个额外的真实性元素,受害者已经信任了最初的攻击源,也很可能会同意并按照指示继续下去。当然,由于受害者在不知情的情况下向攻击者提供了这些敏感的登录细节,攻击者使用它们访问受害者的SaaS帐户,例如,帮助自己访问存储在其中的私有和机密信息。
CHECK POINT RESEARCH — 2019 SECURITY REPORT | 6   
CHECK POINT RESEARCH — 2019 SECURITY REPORT | 8 67% of those who experienced a cyber attack rated its impact as medium or high. Source: Check Point Security Report Threat Prevention Research among IT and Security Professionals, November 2018
N e w T h r e a t s Tr a n s i t i o n t o t he C l o u d Along with a wide range of benefits, thecloud infrastructure introduces a new, fertile and attractive environment forattackers who crave the enormous amount of available computing resources andsensitive data it holds. Indeed, 2018 has brought us various sophisticatedtechniques and tools exploited against cloud storage services. 除了广泛的好处之外,云基础设施还为渴望获取大量可用计算资源和敏感数据的攻击者引入了一个新的、丰富的和有吸引力的环境。事实上,2018年给我们带来了各种针对云存储服务的复杂技术和工具。 Several cloud-based attacks, mainlythose involving data exfiltration and information disclosure, derived from poorsecurity practices. Credentials left available on public source coderepositories or the use of weak passwords are just some examples of how threatactors gained access and control over unprotected resources hosted in thecloud. 一些基于云的攻击(主要涉及数据泄露和信息泄露)源自糟糕的安全实践。公共源代码存储库中可用的凭证或弱密码的使用只是一些例子,说明了威胁参与者是如何获得对托管在云中的不受保护资源的访问和控制的。
Another rising threat taking the cloud environment by stormare cryptominers, targeting the cloud infrastructure in order to exploit thevast computational power it presents and generate huge profits for cybercriminals.
云环境面临的另一个日益严重的威胁是密码破解者,他们瞄准云基础设施,以利用其提供的巨大计算能力,为网络犯罪分子创造巨额利润。 Application Programming Interfaces(APIs) that are used to manage, interact and extract information from serviceshave also been a target for threat actors. The fact that cloud APIs areaccessible via the Internet has opened a window for threat actors to takeadvantage and gain considerable access to cloud applications. 用于管理、交互和从服务中提取信息的应用程序编程接口(api)也一直是威胁行动者的目标。云api可以通过Internet访问这一事实为威胁行动者打开了一个窗口,使他们能够利用并获得对云应用程序的大量访问。 As time passes, threats to the cloudwill continue to evolve. Attackers will continue to develop more and more toolsfor their cloud playground, pushing the limits of the public cloud services.Indeed, as new cloud exploitations emerge, there is no doubt that the nextattack is already taking place. 随着时间的推移,对云的威胁将继续演变。攻击者将继续为他们的云平台开发越来越多的工具,突破公共云服务的极限。事实上,随着新的云开发的出现,毫无疑问,下一次攻击已经开始了。 This introduces a whole new environmentin which victims are exposed to more attack vectors that could be exploited bythreat actors trying to find the weakest link that leads to a person ororganization’s data. 这就引入了一个全新的环境,在这个环境中,受害者会暴露在更多的攻击载体之下,而这些攻击载体可能会被威胁行动者利用,试图找出导致个人或机构数据的最薄弱环节。
CHECK POINT RESEARCH — 2019 SECURITY REPORT
|
9 R e q u i r e d P r e v e n t i o n S o l u t i o n s In order to preventsuch phishing attacks, an in-depth security solution is needed to detect suchphishing attempts. A trusted prevention solution can scan the content ofemails, evaluate the trustworthiness of the sender, and maintain speciallyresearched keywords and a list of other such variables. 为了防止这种网络钓鱼攻击,需要一个深入的安全解决方案来检测这种网络钓鱼企图。一个可信的预防方案可以扫描电子邮件的内容,评估发件人的可信度,并维护专门研究的关键字和其他变量列表。 Whereas manysolutions perform such scanning detections on traffic received from outside ofan organization’s network, what they fail to detect, however, is trafficalready received from within the network. In fact, it’s vital for a solution toscan internal emails from within an organization as phishing scams can beeasily spread from an already compromised account. 尽管许多解决方案对从机构网络外部接收的流量执行这种扫描检测,但是它们没有检测到的是已经从网络内部接收的流量。事实上,从一个机构内部扫描内部邮件对于解决方案来说是至关重要的,因为网络钓鱼诈骗很容易从一个已经被入侵的账户传播开来。
A solution that performs internal scansmust also work in harmony with the existing security of the cloud provider andperform security checks from within the email cloud service. This is somethingthat is not currently done by most of the current solutions available in thecyber security product solutions market. Such security features that come withthe cloud service itself are often shut down.
执行内部扫描的解决方案还必须与云提供商的现有安全性协调工作,并在电子邮件云服务中执行安全性检查。这是目前网络安全产品解决方案市场上的大多数现有解决方案都没有做到的。云服务本身附带的此类安全特性通常会被关闭。 Before aprevention solution is adopted, it’s vital to ensure your IT environment isclean. This can be accomplished by your cloud security solution’s anomalymonitoring that monitors and detects anomalies such as forwarding rules, i.e.,a compromised account sending malicious emails to external users. 在采用预防解决方案之前,确保您的IT环境是干净的是非常重要的。这可以通过云安全解决方案的异常监视来实现,该异常监视和检测异常,如转发规则(?),例如,向外部用户发送恶意电子邮件的受攻击帐户。 In order toprevent account takeovers, any device granted access to the SaaS platform mustbe clean and compliant with the security policy of the company to preventdevices with malware or OS exploits from logging in. 为了防止账户被接管,任何被授权访问SaaS平台的设备必须是干净的,并符合公司的安全策略,以防止恶意软件或OS漏洞的设备登录。 Of course,detection by itself is never sufficient. Prevention is preferred so your cloudsecurity solution protects the last line of defense in your network securityarchitecture. By applying identity protections, your solution can preventunauthorized access to accounts. Such identity protections must be able todeflect phishing attempts and yet still be easy to deploy with zero friction tousers. 当然,仅仅检测是不够的。最好采取预防措施,以便您的云安全解决方案能够保护网络安全体系结构中的最后一道防线。通过应用身份保护,您的解决方案可以防止未经授权的帐户访问。这样的身份保护必须能够转移钓鱼企图,同时仍然易于部署,对用户没有影响。 Mobile security is a major securityconcern these days — and for good reason. Nearly all employees now routinelyaccess corporate data from smartphones, and the challenge is to keep sensitiveinformation out of the wrong hands. 如今,移动安全是一个主要的安全问题,这是有原因的。 如今,几乎所有员工都经常通过智能手机访问公司数据,而挑战在于如何保证让敏感信息不落入坏人之手。
The main security challenge with mobiledevices is that they are easy to overlook. Today’s smartphones are mobile computersthat have been pressed into action by businesses throughout the world. This hasmade network security a bigger and more diverse challenge. The use of mobiledevices and apps has also added a new range of attack vectors and additionalsecurity challenges for IT. 移动设备的主要安全挑战是它们很容易被忽视。今天的智能手机是移动电脑,已经被世界各地的企业付诸行动。这就给网络安全带来了更大、更多样化的挑战。移动设备和应用的使用也为其增加了一系列新的攻击载体和额外的安全挑战。 The proliferation of personalsmartphones and tablets in the workplace exposes your company to increasedrisks. While a breach of personally identifiable information or payment carddata is certainly a top concern for many businesses, there are other risks thatorganizations need to consider. Chief among these are the cost of breaches andresponding to incidents, the potential damage to brand reputation, and a lossof competitive advantage if valuable trade secrets or intellectual propertybecome public knowledge. 随着个人智能手机和平板电脑在工作场所的普及,你的公司面临的风险也在增加。虽然个人身份信息或支付卡数据的泄露无疑是许多企业最关心的问题,但机构还需要考虑其他风险。其中最主要的开销是被侵入和应对事件的成本、对品牌声誉的潜在损害,以及如果有价值的商业秘密或知识产权成为公众知识,将丧失的竞争优势。
Mobile systems, the networks they connect to, and theapplications they run can all be exploited to steal sensitive information suchas documents, calendar appointments, email messages, texts, and attachments. AsCheck Point Research illustrated via announcements of threat actors takingadvantage of the World Cup last year to spy on government agencies throughmalicious mobile applications, cyber criminals can use the smartphone in otherways. A device’s microphone and camera can be used to spy on their targets, andthen send recordings to a secret remote server. They can also capture usernames and passwords as users log in to corporate systems containing sensitivedata.
移动系统、它们连接的网络以及它们运行的应用程序都可以被用来窃取敏感信息,比如文档、日历约会、电子邮件消息、文本和附件。正如Check Point的研究所表明的那样,网络犯罪分子可以通过其他方式使用智能手机,比如利用去年的世界杯(World Cup),利用恶意移动应用程序对政府机构进行间谍活动。设备的麦克风和摄像头可以用来监视目标,然后将录音发送到一个秘密的远程服务器。当用户登录到包含敏感数据的公司系统时,它们还可以捕获用户名和密码。 With this in mind, let us take a closerlook at the four major threats to mobile security in today’s corporateenvironment. 考虑到这一点,让我们仔细看看当今企业环境中移动安全面临的四大威胁。 CHECK POINT RESEARCH — 2019 SECURITY REPORT
|
11 59%
of IT Professionals do not use Mobile Threat Defense. Source: Check Point Security Report Threat PreventionResearch among IT and SecurityProfessionals, November 2018 Tr o j a n s a n d M a l w a r e 特洛伊木马和恶意软件 Social engineering scams remainastonishingly effective. In fact, trickery is just as troubling on the mobilefront as it is on desktops. 社会工程诈骗仍然惊人地有效。事实上,欺骗在移动端和在桌面端一样令人不安。 Many mobile users are unaware of thedangers and they are far too trusting when clicking on links they receive viaSMS or social media apps such as WhatsApp. This can often lead to the devicegetting infected by a wide array of mobile malware. 许多手机用户没有意识到这些危险,当他们点击通过短信或WhatsApp等社交媒体应用程序接收到的链接时,他们过于信任。这通常会导致设备被大量的移动恶意软件感染。
Trojans, for example, carried within an app or installedthrough an unsecured network connection, infect a device with malicious codethat may conduct surveillance by eavesdropping and recording conversations,extracting call logs, tracking locations, logging keyboard activity, andcollecting passwords.
例如,木马病毒在应用程序中携带或通过不安全的网络连接安装,它会用恶意代码感染设备,这些恶意代码可能通过窃听和记录对话、提取通话记录、跟踪位置、记录键盘活动和收集密码来进行监视。 Only
9%of IT Professionals Consider Threats on Mobile a Significant Risk. Source: Check Point Security Report Threat PreventionResearch among IT and SecurityProfessionals, November 2018 F a k e A p p s Malicious apps can take control ofmobile devices and although the app may not appear to be malicious, users maynot notice or understand the permissions they grant during installation. What’smore, even popular apps can be reverseengineered and injected with maliciouscode, and then uploaded to an app store under a different name. 恶意应用程序可以控制移动设备,尽管该应用程序可能看起来没有恶意,但用户可能不会注意到或理解他们在安装过程中授予的权限。更重要的是,即使是流行的应用程序也可以反向工程,注入恶意代码,然后以不同的名称上传到应用程序商店。 Criminals can also create seeminglyauthentic copies of apps that include similar icons, descriptions, screenshots,and even user reviews. But, of course, they don’t work as intended. Instead,victims receive a malicious payload, such as a subscription to an expensive textingservice or a stealthy surveillance tool. Indeed, malicious apps can enable ahost of activities, such as remotely seizing control of the device’s camera andmicrophone to spy on users and their surroundings. Such were the apps the CheckPoint Research team came across on multiple occasions throughout 2018, provingjust how prevalent these highly invasive apps are. 罪犯还可以创建看似真实的应用程序副本,包括类似的图标、描述、屏幕截图,甚至用户评论。但是,当然,它们并不像预期的那样工作。相反,受害者接收恶意负载,如订阅昂贵的短信服务或隐秘的监控工具。事实上,恶意应用程序可以进行一系列活动,比如远程控制设备的摄像头和麦克风,监视用户及其周围环境。这就是Check Point研究团队在2018年期间多次遇到的应用,证明了这些高度入侵的应用是多么普遍。
CHECK POINT RESEARCH — 2019 SECURITY REPORT | 12
M a n - i n - t h e - M i d d l e A t ta c k s Man-in-the-Middle attacks can eavesdrop,intercept and alter traffic between two devices. You believe you’re interactingwith a known and trusted entity, but in fact an attacker is copyingcredentials, snooping on instant messages, or stealing sensitive information.The familiar alert and warning signs on PCs and laptops are far more subtle andeasily overlooked on mobile devices. Small screen sizes can also hide webaddresses, making it harder to validate the address the browser is pointing to. 中间人攻击可以窃听、拦截和改变两台设备之间的通信。您认为您正在与一个已知且受信任的实体进行交互,但实际上攻击者正在复制凭证、窥探即时消息或窃取敏感信息。pc和笔记本电脑上常见的警报和警告信号在移动设备上要微妙得多,也很容易被忽略。小屏幕还可以隐藏web地址,这使得验证浏览器所指向的地址变得更加困难。 Public Wi-Fi hotspots, which areconvenient for internet access, are easy to fake. An attacker can create aspoofed Wi-Fi network, or eavesdrop and alter a legitimate network’s encryptedcommunications by using spoofed certificates or downgrading the communicationlink so that it is no longer encrypted. The attacker can then interceptcommunications, alter data in transit or install a Trojan. 公共Wi-Fi热点,方便上网,容易伪造。攻击者可以创建一个欺骗的Wi-Fi网络,或者使用欺骗证书或降低通信链路的等级,从而窃听和改变合法网络的加密通信,使其不再加密。攻击者可以拦截通信,改变传输中的数据或安装木马。
S y s t e m V u l n e r a b i l i t i e s
Each version of an operating system fora mobile device offers vulnerabilities that cyber criminals can use to launchattacks. Unfortunately, as new versions are notoriously late to market,critical security updates might not make it through testing for weeks or evenmonths, leaving users exposed. 移动设备操作系统的每个版本都提供了网络罪犯可以用来发动攻击的漏洞。不幸的是,由于新版本上市的时间非常晚,关键的安全更新可能无法通过几周甚至几个月的测试,从而使用户暴露在风险之下。 Android is particularly vulnerable. Thethousands of different types of Android smartphones and tablets are not updatedconsistently and at the same time. Most devices are still using older Androidversions in which vulnerabilities have not been patched. Android尤其脆弱。成千上万种不同类型的Android智能手机和平板电脑并不是同时更新的。大多数设备仍在使用旧的Android版本,其中的漏洞尚未修补。 Apple’s iOS, on the other hand, is less vulnerablebecause Apple makes only a handful of different devices and consistentlyprompts users to update them. However, the number of attacks carried out onApple’s iOS is increasing due to the more sophisticated types of attacks thatare carried out on this operating system. 另一方面,苹果的iOS系统不那么容易受到攻击,因为苹果只生产少数几种不同的设备,并不断地提醒用户更新。然而,由于在苹果iOS操作系统上实施的攻击类型更为复杂,针对该操作系统的攻击数量正在增加。
CHECK POINT RESEARCH — 2019 SECURITY REPORT
|
13 There is no doubt that today’s world isbecoming ever more interconnected, so much so that we should perhaps no longertalk so much about the Internet of Things (IoT) but rather the Internet ofEverything. Whether it is agriculture, manufacturing or healthcare, almostevery industry is embracing the proliferation of smart devices available tothem to get deeper insights and more data to aid them in their work. 毫无疑问,当今世界正变得越来越相互联系,以至于我们或许不应该再过多地谈论物联网,而应该谈论万物联网。无论是农业、制造业还是医疗保健业,几乎每个行业都在接受智能设备的普及,以便获得更深入的见解和更多的数据,以帮助他们开展工作。 IoT devices make our lives easier. Smarthome technology, for example, can help users improve energy efficiency byenabling them to turn on (and off) lights and appliances with the tap of atouchscreen. Some connected devices, such as smart medical equipment and alarmsystems, can even help save lives. 物联网设备让我们的生活更容易。例如,智能家居技术可以帮助用户提高能源效率,使他们能够通过轻触触摸屏来打开(或关闭)灯和电器。一些相连的设备,如智能医疗设备和报警系统,甚至可以帮助挽救生命。 Take medical devices, for example. Thissubset of IoT belonging specifically to healthcare and its supportingtechnologies, the Internet of Medical Things, is made up of smart, connecteddevices that automatically collect, process, and digitally relay informationfrom the physical world through a shared network infrastructure. 以医疗器械为例。物联网的这个子集专门属于医疗保健及其支持技术,即医疗物联网(Internet ofMedical Things),它由智能的、相互连接的设备组成,这些设备通过共享的网络基础设施自动收集、处理和数字中继来自物理世界的信息。
Networked medical devices give healthcare professionals theability to be much more accurate with their treatment regimens, far moreefficient in administering care, and way quicker collecting and responding tobiomedical information.
网络医疗设备使医疗专业人员能够更准确地制定治疗方案,更有效地进行护理,更快地收集和响应生物医学信息。 There will be an estimated
125 million
Healthcare IoT devices in 2019. Source:Statistica.com, Estimated Healthcare IoT DeviceInstallations As a result, IoMT technologies arecurrently exploding, both in terms of their popularity and capabilities. Putsimply, IoMT is redefining the practice of medicine. And while this new frontierof medicine is very exciting and hugely promising, it is not without itsproblems. 因此,IoMT技术目前正在迅猛发展,无论是在受欢迎程度还是在能力上都是如此。简而言之,IoMT正在重新定义医学实践。尽管这一医学新领域非常令人兴奋,前景广阔,但也并非没有问题。 There are also serious security risksassociated with IoT technology. As the IoT ecosystem expands, so does theattack surface for cyber criminals. In other words, the more we rely onconnected technology in our day-to-day lives, the more vulnerable we are to thecyber threats that are increasingly tailored to exploit vulnerabilities andsecurity design flaws in IoT devices. 物联网技术也存在严重的安全风险。随着物联网生态系统的扩张,网络犯罪的攻击也浮出水面。换句话说,我们在日常生活中对互联技术的依赖程度越高,我们就越容易受到网络威胁的影响,这些威胁越来越多地针对物联网设备的漏洞和安全设计缺陷量身定制。
CHECK POINT RESEARCH — 2019 SECURITY REPORT | 14
This presents a daunting challenge for cybersecurity professionals. They must not only protect their own devices, but they must also defend against threats targeting external machines that might connect to their IT networks as a whole. 这对网络安全专业人士提出了严峻的挑战。它们不仅必须保护自己的设备,而且还必须防范针对可能连接到整个IT网络的外部机器的威胁。 The current IoT landscape then can be compared to the early days of the internet, when viruses, worms, and email spam plagued users. Many companies raced to join the internet ‘gold rush’ without necessarily considering the importance of internet security. 现在的物联网可以与互联网早期相比,那时病毒、蠕虫和垃圾邮件困扰着用户。许多公司没有考虑到网络安全的重要性,就争先恐后地加入了互联网“淘金热”。 T h e S e c u r i t y I s s u e s While the concerns regarding medical IoT devices may be more particular, the major malfunction with IoT device security as a whole lies in the fact that they are usually poorly coded. This is mainly due to the device manufacturers’ pursuit of profitability over user security. So when insecure devices are connected to the open internet, they become the route for a disaster waiting to happen. 虽然人们对医疗物联网设备的担忧可能更为具体,但物联网设备安全性的主要故障在于它们的编码通常很糟糕。这主要是由于设备制造商追求的是盈利而非用户安全。因此,当不安全的设备连接到开放的互联网时,它们就会成为等待灾难发生的路径。 For example, cyber criminals can hack insecure security cameras or other smart devices and use them to access the rest of an organization’s corporate or individual’s home network. Alternatively, thousands of these insecure IoT devices can be combined to form a zombie botnet army to launch devastating DDoS attacks. 例如,网络罪犯可以破解不安全的安全摄像头或其他智能设备,并利用它们来访问机构的其他企业或个人的家庭网络。或者,成千上万的不安全的IoT设备可以组合成一个僵尸网络,以发动破坏性的DDoS攻击。 In addition, IoT devices themselves can be exploited to give threat actors unauthorized entry, as illustrated by Check Point’s research into LG automatic vacuum cleaners that showed how a hacker could take over the device’s camera to spy on users. However it is often forgotten that the data collected by these devices is usually stored in the cloud. In this respect, as shown by recent research into drones, an attack on the IoT-Cloud infrastructure could leave photos and film footage taken by the drone devices exposed to theft. This is just one example of how sensitive data stored in the cloud could be breached, though with so much data collected by IoT devices as a whole, organizations should be extremely cautious about how that data is stored. 此外,物联网设备本身也可以被利用,使威胁行动者未经授权进入,Check Point对LG自动吸尘器的研究就证明了这一点。该研究显示,黑客可以利用该设备的摄像头来监视用户。然而,人们常常忘记,这些设备收集的数据通常存储在云中。在这方面,正如最近对无人机的研究所显示的那样,对IoT-Cloud基础设施的攻击可能会使无人机设备拍摄的照片和视频片段暴露在盗窃的风险之下。这只是云中存储的敏感数据如何被破坏的一个例子,尽管作为一个整体,物联网设备收集了如此多的数据,组织应该对这些数据的存储方式非常谨慎。 Another hurdle IT professionals face with regard to network compliance is the sheer lack of regulation surrounding the entire IoT ecosystem. Though there may soon be IoT regulations in the state of California, which is leading the way in the area of IoT regulations, it is currently the responsibility of IT professionals to audit devices for compliance. Regardless of these regulations, there will continue to be millions of devices still in use from before these new requirements come into force, which will still have a large potential for exploiting the weaknesses in these outdated devices. IT专业人员在网络遵从性方面面临的另一个障碍是整个物联网生态系统完全缺乏监管。尽管在物联网法规领域处于领先地位的加利福尼亚州可能很快就会出台物联网法规,但IT专业人员目前的职责是对设备进行合规审计。无论这些规定如何,在这些新要求生效之前,仍将有数百万台设备在使用,这些设备仍有很大潜力利用这些过时设备的弱点。 CHECK POINT RESEARCH — 2019 SECURITY REPORT | 15   Thecloudenvironmenthaschangedthewaycompaniesmanage,storeandsharetheirdata,applications,andworkloads.Alongwithawiderangeofbenefits,though,thecloudinfrastructurealsointroducesanew,fertileandattractiveenvironmentforattackerswhocravetheenormousamountofavailablecomputingresourcesandsensitivedataitholds. Whileweconsiderthecloudtobeanorganization’sweakestlink,threatsposedtothemviatheiremployee’smobileandIoTdevicesarealsotobetakenseriouslyasoneofmanyattackvectorsfromwhichsensitivedatacanbestolenorleveragedtolaunchanattack. Inthenextandfinalinstallmentofthis2019SecurityReport,wewillbeprovidingsomerecommendationsonhoworganizationscanpreventtheseinvasiveanddamagingattacksfromoccurring.Consideringthedirectionthethreatlandscapehastakensofar,wewillalsobemakingsomepredictionsaboutwhatwecanexpecttoseeintheyearahead. 云环境改变了公司管理、存储和共享数据、应用程序和工作负载的方式。然而,除了广泛的好处之外,云基础设施还为渴望获取大量可用计算资源和敏感数据的攻击者引入了一个新的、丰富的和有吸引力的环境。
Fertile 肥沃、丰富 虽然我们认为云计算是一个机构最薄弱的环节,但通过员工的移动设备和物联网设备对他们构成的威胁也应该被认真对待,因为它是许多攻击载体之一,敏感数据可能会被窃取或利用来发动攻击。
在2019年安全报告的下一篇也是最后一篇中,我们将提供一些关于机构如何防止这些侵入性和破坏性攻击发生的建议。考虑到目前为止威胁景观的发展方向,我们还将对未来一年的我们能期望看到的情况做出一些预测。 
附录一
2019年,注定会成为云计算发展历程中里程碑式的一年。在全球范围中,云平台已经从单纯IT资源,转变为企业谋求发展的新引擎。著名咨询机构Forrester在其预测中指出:云计算在今年将真正成为企业完成数字化转型的核心基础。在我国,随着5G的商用化推进,物联网、大数据等新兴科技的快速发展,云计算...
2019年,注定会成为云计算发展历程中里程碑式的一年。在全球范围中,云平台已经从单纯IT资源,转变为企业谋求发展的新引擎。著名咨询机构Forrester在其预测中指出:云计算在今年将真正成为企业完成数字化转型的核心基础。在我国,随着5G的商用化推进,物联网、大数据等新兴科技的快速发展,云计算将迎来井喷期。在工信部2017年印发的《云计算发展三年行动计划(2017-2019年)》中提出:到2019年我国云计算产业规模将达到4300亿元,要建立云计算公共服务平台,支持软件企业向云计算加速转型,加大力度培育云计算骨干企业,建立产业生态体系。然而,随着云计算的普及,基于云且针对云的安全威胁则成为了IT决策者不得不面对的新挑战。企业如何在云端获取利益的同时,能够最大程度避免云端威胁带来的损失?Check Point 中国区总经理陈欣先生通过分析《2019年安全报告》,提出了宝贵的建议。
陈欣先生指出:云安全已经成为IT安全领域最受瞩目的话题。在即将召开的2019 RSA大会上,主办方给出的议题列表中,云安全成为了提及率最高的话题。这充分表明了IT安全从业者已经意识到,由于云强大的灵捷性与扩展性,以及企业对云原生应用依赖度的提升,云端威胁与云安全策略与传统网络安全有着本质的区别。在传统网络安全领域一直有“天下武功唯快不破”的说法,但在Check Point看来,快速反应不足以应对针对云的安全威胁,如何从“快”到“先”,才是解决这些威胁的关键。 作为全球领先的政府与企业网络安全供应商,Check Point 不仅拥有经验丰富的研发团队,更拥有一支享誉业内的特种部队 -- Check Point Research。该团队由 100 多名分析师和研究人员组成,能够与其他安全厂商、执法机关及各个计算机安全应急响应组展开合作, 并通过收集和分析 ThreatCloud 存储的全球网络攻击数据,在防范黑客的同时,确保所有 Check Point 产品都享有最新保护措施。陈欣先生表示,Check Point Research最近发布的《2019年安全报告》对云安全以及整个IT安全都有着战略上的警示意义。该报告指出,在过去一年,全球内18%的机构由于云端威胁遭受了损失。数据丢失与窃取、未授权登入与API管理将成为云安全防御的主要工作。更值得注意的是,仍有30%的IT安全从业者认为云安全应有云服务提供商负责,高达59%的IT人员没有考虑实施移动设备安全策略。这在混合云方兴未艾,各种智能设备普及的今天,无疑对企业的云平台带来了更大的潜在危险。在动机上,经济利益成为了攻击者的首要驱动力。随着加密数字货币价值的飙升,2018年企业受到恶意挖矿软件的的侵害约为勒索软件的十倍。恶意软件即服务(Malware-as-a-service)模式的兴起使网络攻击成为更加云化且成熟的产业链。 陈欣先生最后强调,云的普及使我们必须以更加前瞻的视角审视企业的安全策略。通过不断的总结与合理的分析、以及与云生态系统中其他环节厂商的紧密合作,Check Point将为用户交付更加智能、具有高度弹性且能够面对未来潜在威胁的云端安全解决方案。
附录二
MAESTRO HYPERSCALE ORCHESTRATOR
Check Point Maestro brings scale, agility and elasticityof the cloud on premise with efficient N+1 clustering based on Check Point HyperSync technology, maximizing thecapabilities of your existing security gateways. Create your own virtualizedprivate-cloud premise by stacking multiple Check Point security gatewaystogether. Group them by security feature set, policy or the assets they protect and furthervirtualize them with virtual systems technology. With the Maestro Hyperscale Orchestrator, businesses of all sizes can havecloud-level security on premise. Add compute to meet your needs usingMaestro Web UI or RESTful APIs – all while minimizing the risk ofdowntime and maximizing your cost efficiency.
Check Point Maestro以高效的N+1集群为基础,在保证云计算规模、敏捷性和弹性的前提下实现Check point超同步技术,最大化现有安全网关的功能。通过将多个checkpoint安全网关堆叠在一起,创建您自己的虚拟私有云前提。按安全性分组特性集、策略或它们保护的资产,并使用虚拟系统技术进一步虚拟化它们。 与Maestro超大规模的协调器,任何规模的企业都可以拥有云级别的安全性。使用Maestro Web UI或RESTful api添加计算来满足您的需求——同时最小化停机风险并最大化您的成本效率。
MAESTRO HYPERSCALE ORCHESTRATOR
The Hyperscale Orchestrator140 is a mid-range model with 48x 10GbE and 8x 100 GbE ports with a totalfabric capacity of 2 to 4 Tbps. The Hyperscale Orchestrator 170 is a high-endmodel with 32x 100 GbE ports and a total fabric capacity of 3.2 to 6.4 Tbps.
Hyperscale Orchestrator 140是一款中档型号,拥有48x 10GbE和8x 100 GbE端口,总织物容量为2至4 Tbps。Hyperscale Orchestrator 170是一款高端机型,拥有32x 100 GbE端口,总织物容量为3.2至6.4 Tbps。 For additional capacity,deploy two Orchestrators of the same model together. Security Group membersconnect to the Orchestrator via Direct Attached Cables (DAC), either 10 GbE or40 GbE depending upon the gateway and Orchestrator models deployed. The Orchestrator’s300nanosecond port-to-port latency deliver predictable wire speed performancewith no packet loss for any packet size. 要获得额外的能力,可以将相同模型的两个协调器部署在一起。安全组成员通过直接连接电缆(DAC)连接到编排器,根据部署的网关和编排器模型,可以是10 GbE,也可以是40 GbE。编排器的300纳秒端口到端口延迟提供了可预测的线速度性能,并且对于任何包大小都没有包丢失。
SECURITY GROUPS With Maestro, you candynamically allocate or deallocate compute resources within and betweenSecurity Groups to meet your needs. Security Groups are logical groups ofappliances providing active/active cluster functionally segregated from otherSecurity Groups. Each Security Group has dedicated internal and externalinterfaces and may have a different configuration set and policy, e.g. NextGeneration Firewall protecting a data center or Next Generation ThreatPrevention providing perimeter protection. 使用Maestro,您可以在安全组内部和安全组之间动态分配或释放计算资源,以满足您的需求。安全组是提供与其他安全组在功能上隔离的活动/活动集群的设备的逻辑组。每个安全组都有专用的内部和外部接口,并且可能有不同的配置集和策略,例如保护数据中心的下一代防火墙或提供周界保护的下一代威胁预防。
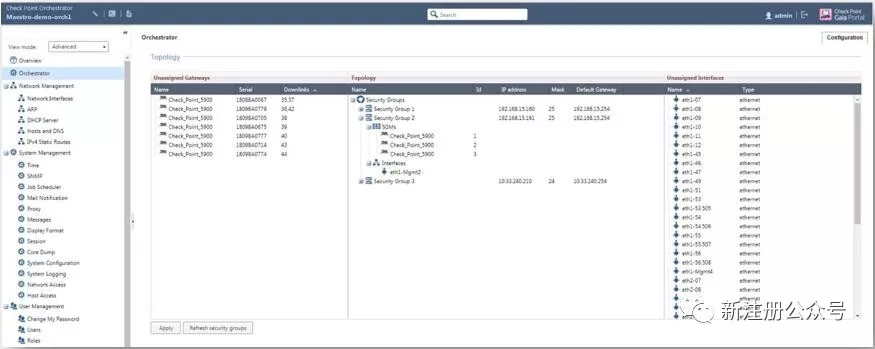
SINGLE MANAGEMENT OBJECT (SMO) Externally a Security Groupis seen as one security gateway or VSX gateway object in the Check Pointsecurity management GUI client, SmartConsole. A single IP address per SecurityGroup for management communications and policy install simplifies SecurityGroup management. All configurations, e.g. interfaces or IP addresses and routesare mirrored on gateways in the Security Group. Prior to becoming an onlinemember and actively handling traffic each new member of the Security Groupsynchronizes its image, software configuration and security policy with the SMOof the Security Group. 在外部,安全组被视为checkpoint安全管理GUI客户机SmartConsole中的一个安全网关或VSX网关对象。用于管理通信和策略安装的每个安全组的一个IP地址简化了安全组管理。所有配置,例如接口或IP地址和路由都镜像在安全组中的网关上。在成为在线成员并积极处理流量之前,安全组的每个新成员都将其映像、软件配置和安全策略与安全组的SMO同步。
SECURITY SOFTWARE Maestro members run R80.20SP,the latest version of the field-tested and proven software that was firstintroduced in 2012 on our Check Point chassis security systems and nowintegrated into our R80.x main train release. Maestro成员运行R80.20SP,最新版本的现场测试和验证软件,2012年首次引入我们的checkpoint chassis安全系统,现在集成到我们的R80.x主发行版本。
This includes Next GenerationThreat Prevention (NGTP) and NGTP plus SandBlast Zero-day Threat Protection toprotect you from the unknown threats. 这包括下一代威胁预防(NGTP)和NGTPsandblast零日威胁保护,以保护您来自未知的威胁。
With R80.20SP, you canmonitor and manage the Maestro security fabric. Easily see the state of thegateways and the overall performance of your Security Group members. 使用R80.20SP,您可以监视和管理Maestro安全结构。轻松查看网关状态和安全组成员的总体性能。
Do advanced configurationsuch as setting up network bonds, image management and system optimization. 进行高级配置,如建立网络连接、图像管理和系统优化。
MAESTRO USER INTERFACE
SPOTLIGHTHyperscale Security System With Maestro, you can startwith 8.9 Gbps, but you can grow, you can easily add existing AND new gateways,up to 52 of them, on demand, and for example, when you start with 8.9 Gbps youcan finish with a 450 Gbps security solution. Simply by using Check PointMaestro.
使用Maestro,你可以从8.9 Gbps开始,但是你可以增长,你可以很容易地添加现有的和新的网关,多达52个,可以根据需要,例如,当你从8.9 Gbps开始,你可以用450 Gbps的安全解决方案结束。只需使用CheckPoint Maestro.
HyperscaleOrchestrator
Fully Operational
Connectionswithin Minutes
When a Security Group is created
When we add a gateway
to the system, it gets all an IP address iscreated for the
theconfigurations, the SMO management interface
policy, even the software connection to thesecurity
version, updatedand management server. Easily create
aligned with the existing and assign IPaddresses to the
deployment, readyto go internal and external network
within 6 minutes. interfaces.These uplinks are the
visiblecomponents of the Maestro
security architecture.
创建安全组时,当我们添加网关时对于系统,它获取为配置、SMO管理接口策略、甚至到安全版本、更新和管理服务器的软件连接创建的所有IP地址。轻松创建与现有网络一致的IP地址,并为部署分配IP地址,准备在6分钟好进入内部和外部网络,接口。这些上行链路是Maestro安全架构的可见组件。
Maestro TrafficCost-Efficient
DistributionN+1 Deployments
HyperSync tracks the We can have an efficient
Active/Standby/Backup state of N+1 clustering
group members, limiting sync deployment, underone
traffic to only the Active and unified systemwith the
Standby members,which are Maestro Security
handling the connection. Orchestrator. Now
Unicast packets results in a businesses of allsizes
reduction of sync traffic canenjoy cloud-level
overhead across the Maestroresiliency and telcosecurity architecture. gradetechnology.
HyperSync跟踪我们可以拥有N+1集群组成员的有效活动/备用/备份状态,将同步部署限制在1个以下
流量只到活动和统一的系统与备用成员,这是大师安全处理连接。协调器。现在,单播数据包带来了各种规模的业务,减少了同步流量,可以享受跨Maestro弹性和telco安全架构的云级开销级技术。
Step Up to 5th
Generation Cyber Security Gen V securityleaves the patchwork and bestInstead, it’s characterized by an architecturethat unifies allnetworks, cloud, and mobile-of-breed deployments of the past behind.
devices, supported by real time threatintelligence.
第五代的安全系统留下了补丁,取而代之的是最好的,它的特点是将过去所有的网络、云和移动部署统一起来。设备,由实时威胁情报支持。 ORDERING MAESTRO HYPERSCALEORCHESTRATOR
MAESTRO HYPERSCALE SOLUTION PACKAGES | SKU | Maestro Solution with two 23800 Security Gateways and one Orchestrator (MHO-170), including cables | CPAP-MHS-23802 | Maestro Solution with three 23800 Security Gateways and one Orchestrator (MHO-170), including cables | CPAP-MHS-23803 | Maestro Solution with two 6800 Security Gateways and one Orchestrator (MHO-140), including cables | CPAP-MHS-6802 | Maestro Solution with three 6800 Security Gateways and one Orchestrator (MHO-140), including cables | CPAP-MHS-6803 | Maestro Solution with two 6500 Security Gateways and one Orchestrator (MHO-140), including cables | CPAP-MHS-6502 | Maestro Solution with three 6500 Security Gateways and one Orchestrator (MHO-140), including cables | CPAP-MHS-6503 |
SECURITY GATEWAY APPLIANCES FOR SCALE-UP | SKU | 23800 Security Gateways for Maestro including NGTP subscription for the first year, one 40 GbE NIC and two 40 GbE direct attach cables (DAC) | CPAP-SG23800-MHS | 6800 Security Gateways for Maestro including NGTP subscription for the first year, one 10 GbE NIC and two 10 GbE direct attach cables (DAC) | CPAP-SG6800-MHS | 6500 Security Gateways for Maestro including NGTP subscription for the first year, one 10 GbE NIC and two 10 GbE direct attach cables (DAC) | CPAP-SG6500-MHS |
MAESTRO HYPERSCALE ORCHESTRATORS | SKU | Maestro Hyperscale Orchestrator 140 with 8x 100 GbE and 48x 10 GbE ports | CPAP-MHO-140 | Maestro Hyperscale Orchestrator 170 with 32x 100 GbE ports | CPAP-MHO-170 |
MAESTRO HYPERSCALE ORCHESTRATORS ACCESSORIES | SKU | Fan replacement for Maestro Hyperscale Orchestrator 170 | CPAC-FAN-MHO170 | Fan replacement for Maestro Hyperscale Orchestrator 140 | CPAC-FAN-MHO140 | AC power supply unit replacement for Maestro Hyperscale Orchestrator 140 and 170, with front to back airflow | CPAC-PSU-ACMHO140/170 | Rail kit for Maestro Hyperscale Orchestrators 140 and 170 | CPAC-RAIL-MHO140/170 |
DIRECT ATTACH CABLES | SKU | Direct Attach Cable (DAC) 10GbE SFP+ to SFP+, 1M | CPAC-DAC-10G-1M | Direct Attach Cable (DAC) 10GbE SFP+ to SFP+, 3M | CPAC-DAC-10G-3M | Direct Attach Cable (DAC) 40GbE QSFP to QSFP, 1M | CPAC-DAC-40G-1M | Direct Attach Cable (DAC) 40GbE QSFP to QSFP, 3M | CPAC-DAC-40G-3M | Direct Attach Cable (DAC) 100GbE QSFP28, 3M | CPAC-DAC-100G-3M | Direct Attach Cable (DAC) 40GbE QSFP to 4xSFP+ 3M | CPAC-DAC-40/10G-3M | Direct Attach Cable (DAC) 40GbE QSFP to 4xSFP+ 1M | CPAC-DAC-40/10G-1M |
附录三
以色列网络安全企业捷邦(Check Point)调研
以色列是仅次于美国的第二大网络产品和服务出口国,在以色列政府各项政策的大力支持下,该国的网络安全企业发展具有技术专注、数量众多、投资密集、能力突出等特点,被外界称为第二个硅谷。本文通过对以色列网络安全领域典型企业Check Point的调查研究,阐述了该公司现状,分析了其成长路径和能力影响,进而探索以色列网络安全企业在军民融合背景下的发展规律,以期为国内网安企业开展军民融合、政企合作和创新中国发展模式提供借鉴。
引言 以色列网络安全产业发达、网络安全技术领先,占全球网络安全市场10%左右。当前,在以色列政府各项政策的大力支持下,网络安全初创企业涌现速度快,对资金吸引力强,外资投入占比较大,市场充满活力,企业规模呈现持续递增趋势。在众多以色列网络安全企业中,全球最大的防火墙软件商Check Point具有显著的代表性,从其成长可以了解以色列政府的扶持举措和企业的发展情况。 公司基本情况 以色列Check Point(捷邦)安全软件科技有限公司是全球最大的专注于安全解决方案的提供商之一,成立于1993
年,拥有员工人数2,200人,其国际总部位于以色列特拉维夫,并在美国和其他38个国家设有办事处。该公司为世界各地客户提供业界领先的解决方案,以抵御恶意软件和各种威胁。Check Point凭借防火墙FireWall-1以及获得专利的状态检测技术(Stateful inspection)成为IT安全行业的先驱。 Check Point提供全方位的安全解决方案,包括终端安全解决方案、防火墙、数据安全、从企业网络到移动设备的安全保护以及可视化的安全管理方案等。该公司集成产品为企业员工的个人设备提供从企业边界到云端的端到端安全性防护,阻止并解决网络威胁,防范这些威胁造成的数据窃取,其统一安全管理解决方案具有可扩展性和易用性等特点。 公司成长背景和条件 以色列政府为Check Point公司的发展壮大提供了良好的政策支持和环境平台,其创始人的成长背景则具有明显军民融合的特色,在上述多方作用下,Check Point公司逐年取得成就,成长为以色列乃至全球领先的网络安全公司。 与军方具有天然联系 Check Point的创始人兼首席执行官吉尔·舍伍德(Gil Shwed)被称为“在信息技术领域开拓新前沿——以色列高科技的创始人”。吉尔·舍伍德曾在以色列的8200部队中服役。以色列8200部队相当于美国的国安局,归国防部管辖,负责军方信号情报和代码破译,是以色列国防军中规模最大的独立军事单位,被视为替以色列培养科技人才而成立,也被业内普遍认为是世界上最先进的网络间谍部队。 8200部队既是以色列工控安全厂商商业品牌和技术建立的基础,同时也是这些初创公司的青年人才孵化器。以色列实行全民服兵役的强军体制,该国青年男女在高中或大学毕业后,大多数会选择在军队中接受信息技术和网络安全再教育,成为一名掌握高技术的现代化军人。经过军队的系统训练和实战操作,以色列青年人具有领先于他国的整体计算机水平和网络安全技能,使其转业后能够成为创业大军中的高级职业领军人物。此外,军事需求和军工科研项目对网络安全创业公司有着直接的引领和指导作用,以色列的本土公司能够与国防力量紧密合作,并高效吸引和利用军中涌现出的网络精英。以色列军工企业与民营创业公司有着广泛的合作,不少军工项目的理念也自然融合到网络安全产业之中。 以色列政府的扶持政策 Check Point能够迅速崛起成为全球性网络安全企业离不开以色列政府的政策支持和对产业的大力推动。以色列政府在2011年制定并颁布网络空间国家战略,提出构建网络生态系统,该生态系统由观念理论、政策工具、主管机构、产业平台、人才培养等各种要素组成。多年来以色列政府不断整合政府部门、军情部门、产业界、学术界等优势资源,出台多项政策措施,设计构建多个发展平台,推出系统化的激励政策。 “前进”计划是2013年以色列国家网络局和首席科学家办公室共同推出的网络安全研发促进计划,旨在资助以色列企业研发网络安全技术解决方案,推进国家网络安全产业发展。这也是以色列国家网络局成立后推出的首个促进网络安全产业化发展的计划。在“前进”计划中,以色列政府将发展网络安全产业提升为国家战略,将其视为“国家经济增长的新引擎”。 “前进”计划为期两年半,从2013年1月开始,至2015年6月结束,总投资设定为1亿新谢克尔(约为2700
万美元),由以色列国家网络局、经济部及首席科学家办公室共同出资。此外,首席科学家办公室还设立了11个网络安全产业孵化器。以色列首席科学家艾维·哈森感叹“前进”计划是近年来以色列推出的最好、最抢手的产业促进计划。 集成化的产业园区支撑 除了以色列政府提供的有利大环境,Check Point的发展还依托于以色列创意园区带来的环境利好。该公司所在的特拉维夫工业园是以色列网络安全产业的发源地和技术之都,那里集聚了1200多家高科技公司和近1000家创业小企业。政府创新科技园区的建立和发展,有力支持了以大学为辅助,以众多创新企业为基础,以国防军工为助力,发挥产学研用集群效应的高科技园区,从而将教育、研究、创新、技术、军队、治理、网络和企业文化等自然地融合为一体,这些成熟的机制为网络安全产业发展提供适宜的技术环境、财务支持、实际操作和物流、销售方面的专家建议和行政协助。 公司能力和影响 凭借以色列政府的鼓励举措和该公司创始人的才能,Check Point公司取得了一系列的成果。2006年,Check Point
发明了统一安全构架。此架构采用单一管理控制台、统一安全网关以及首个也是唯一一个为端点安全而设计的单一代理。2009年初,Check Point推出了突破性安全创新技术——软件刀片架构。这是一个动态的、革新性架构,可提供安全、灵活和简单的解决方案,可定制以满足各种组织和环境的具体安全需求。2009年4月,Check Point完成了收购诺基亚安全设备业务,与诺基亚携手为业界提供领先的企业安全解决方案。2009年11月,Check Point完成收购FaceTime Communications的应用数据库,从而取得业界最全面的应用程序分类和签字数据库,可为50,000多个Web 2.0专用界面工具和4,500多种互联网应用程序提供安全控制。 当前,Check Point通过向服务提供商、中小型企业和消费者提供个性化的产品与服务,为全球超过10万个企业和数百万用户提供安全保护。Check Point的合作伙伴包括美国密西西比办公室、三星美国研发部等政府部门和知名企业。 财富500强企业和全球500强企业中有98%的公司使用Check Point的安全解决方案。该公司现在已经获得39项美国专利,超过25项美国专利备案,其他专利正在发布或申报中。1999到2002年间连续四年、2004到2010年间连续七年,Check Point被Gartner集团的“防火墙Magic Quadrant”评为企业防火墙市场的领导者类别第一位。Check Point
是全球最大的防火墙软件商。根据调查机构爱迪西(IDC)的研究指出,Check Point在全球防火墙软件上拥有四分之一的市场占有率。趋势科技(Trend Micro Corp.)总裁张明正曾公开表示,要学习Check Point在专业领域上的执著,甚至希望有机会与这家公司合作。同时,Check Point也是全以色列市值最高的企业,甚至比以色列的航空公司,或是几家大银行合并起来都还要大。 Check Point的发展与以色列国家营造的大环境密不可分,与政府的种种扶持政策息息相关,无论是该企业创始人还是企业自身的发展都得益于以色列政府的大力支持。从企业和产业发展的角度来看,Check Point仅是以色列众多网络安全公司的其中之一,越来越多的企业受益于军民融合的大背景,在外部政策塑造的有利环境中寻求成长和发展。 翻译 SUNYIBO FROM Tianjin University of Technology |